In this information age, inadequate cybersecurity practices can lead to long-term or permanent consequences. This has led to organizations being increasingly particular about protecting themselves from data breaches and hacks. Northwood’s Bachelor of Science in Information Systems and Cybersecurity will allow you to master the art of safeguarding digital data and the skills that are sought-after by employers.
Northwood’s Bachelor of Science in Information Systems and Cybersecurity program is a STEM certified program for Optional Practical Training (OPT) purposes. This means that it offers the potential for international students to work in the US for a total of 3 years and the potential for a work visa (H1-B, etc.) This makes it the perfect platform to launch your career in information systems and cybersecurity.
GET STARTED
Please register below to receive program brochure and connect with a program advisor.

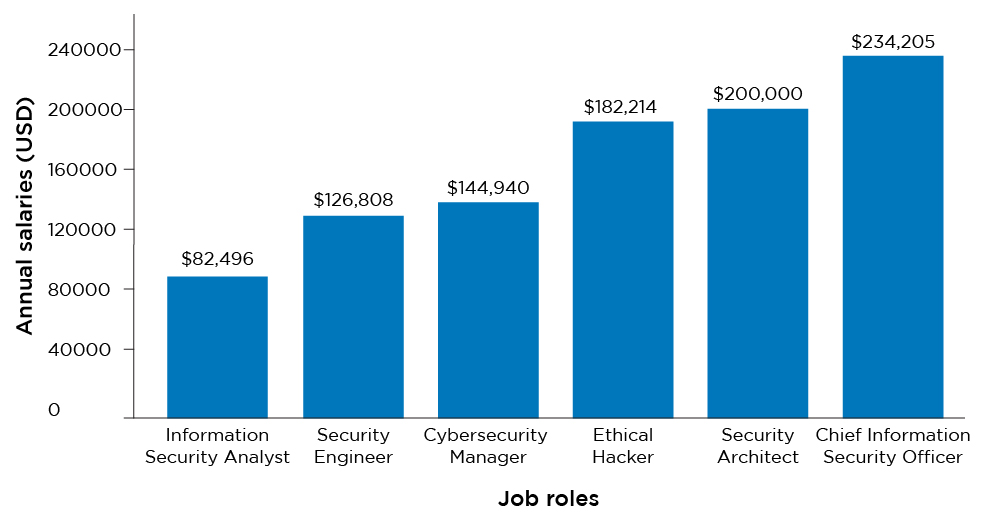
CAREER OPPORTUNITIES
With evolving technologies comes the need to bolster information systems and protect information and businesses against cyber crimes. Here is a glimpse into a career in information systems and cybersecurity:
Here is look at a few primary industries who employ information systems and cybersecurity professionals:

THE NORTHWOOD DIFFERENCE
For over 60 years, Northwood University has prepared students to launch their careers successfully in their selected field. And our holistic approach develops the future leaders of a global free-enterprise society.
At Northwood, you will start classes in your major on your first day. This means you can validate your interest in a major field of study early and be prepared for internships after your first year. During your time at Northwood, you will;

CURRICULUM
The Bachelor of Science in Information Systems and Cybersecurity curriculum is designed to equip students with the skills and knowledge they need to succeed in this rapidly evolving field. You will learn about techniques to protect against cybersecurity threats, as well as the ethical and legal issues involved in securing sensitive information. With a combination of technical and business focus, you will get a hands-on learning experience that will prepare you for success in the industry and showcase your abilities to prospective employers.
- FDN 1110 Student Success Seminar or FDN 2500 Strategies for Success — 1 credit hour
- FDN 1300 Student Leadership Seminar (campus only) — 1 credit hour
- FDN 2250 Blueprint for Success or FDN 3200 Career Advancement — 1 credit hour
General education courses are the foundation of the University’s outcomes and attributes for its graduates.
- ENG 1150 Composition I — 3 credit hours
- ENG 1200 Composition II — 3 credit hours
- MTH 1150 College Algebra or MTH 1100 Finite Math — 3 credit hours
- SPC 2050 Speech — 3 credit hours
- NSC 2100 Environmental Science or Natural Science — 3 credit hours
- HIS 2100 Foundations of the Modern World I or History Elective — 3 credit hours
- MTH 2310 Statistics I — 3 credit hours
- ACC 2410 Fundamentals of Financial Accounting — 3 credit hours
- ACC 2415 Fundamentals of Managerial Accounting — 3 credit hours
- ECN 2210 Principles of Microeconomics — 3 credit hours
- ECN 2220 Principles of Macroeconomics — 3 credit hours
- LAW 3000 Business Law I — 3 credit hours
- MGT 2300 Principles of Management — 3 credit hours
- MIS 1500 Business Productivity Software — 3 credit hours
- MKT 2080 Principles of Marketing — 3 credit hours
- FIN 3010 Financial Management — 3 credit hours
- MGT 4250 Organizational Behavior — 3 credit hours
- MGT 4800 Strategic Planning — 3 credit hours
- PHL 3100 Ethics — 3 credit hours
- ECN 4010 Economics of Public Policies — 3 credit hours
- PHL 4100 Philosophy of American Enterprise — 3 credit hours
- MIS 1110 Introduction to Management Information Systems — 3 credit hours
- MIS 2140 Programming I — 3 credit hours
- MIS 1300 Information Technology Infrastructure — 3 credit hours
- MIS 2150 Programming II — 3 credit hours
- CYB 2150 Scripting — 3 credit hours
- CYB 2300 Advanced Networking Systems — 3 credit hours
- CYB 2350 Software Defined Networking — 3 credit hours
- CYB 3300 Physical and Operational Security — 3 credit hours
- CYB 3000 Cryptography — 3 credit hours
- CYB 3200 Network Security — 3 credit hours
- MIS 3400 Systems Analysis and Design — 3 credit hours
- MIS 3800 Information Security — 3 credit hours
- MTH 3400 Introduction to Data Science — 3 credit hours
- CYB 4100 Ethical Hacking — 3 credit hours
- CYB 3950 Advanced Operational Security — 3 credit hours
- CYB 4000 Digital Forensics — 3 credit hours
- MIS 4500 Technology Senior Project — 3 credit hours
Cybersecurity Management Core Course Descriptions (30 Credits)
Students will develop a thorough understanding of the current operating systems, networks and communications infrastructure. Includes an understanding of the functions of operating systems, fundamental automated data and voice communications concepts and terminology, and modes of data transmission, transmission media, and different types of networks.
By the end of this course, you will be able to:
- Understand the functions of operating systems.
- Understand commercial and private communications media.
- Understand the development and potential future of business communications.
- Understand current software trends for data communications.
- Understand networks and network design fundamentals.
- Understand the function of collaborative software systems.
- Understand how to use the web for business.
Introduces students to the elements of business programming using a selected programming language. Study of the program development cycle and practice designing and writing business application programs. In designing programs, students will learn to identify program requirements, data requirements, user interface requirements and the programming processes needed to develop a solution. Based on their designs, students will code, test and evaluate their programs.
By the end of this course, you will be able to:
- Describe the program and data design methods used in programming.
- Compare the structured, object-oriented and event-driven programming paradigms.
- Identify the elements of business applications.
- Understand syntax and error handling processes in a popular business programming language.
- Describe the steps in the program development cycle: analyze, design, interface, code and test.
- Develop and document programs using programming tools.
- Write computer programs using a Windows-based language.
Students will examine the significant role that project management plays in the successful completion of an information technology project. The skills, tools and best practices used to effectively manage a project from its inception to successful closure will be discussed. Students will learn how to control the scope, time, cost and quality of projects, and gain hands-on experience using project management software.
Prerequisite: MIS 1500
By the end of this course, you will be able to:
- Describe the constraints that affect project management.
- Describe the project management framework, which includes the stakeholders, project management knowledge areas and project management tools and techniques.
- Identify the phases of the project life cycle and compare the project life cycle and the product life cycle.
- Describe the main processes and deliverables in managing a project.
- Effectively use project management software to design a project.
- Work within a group to maximize the group effectiveness of a project.
- Analyze project requirements and develop a complete project plan for a business process change.
Examines the various tools and methodologies for the development and implementation of a business information system. Students will also examine the logical and physical organizations of data in an enterprise database. The systems approach is discussed in detail in conjunction with the current concepts of systems analysis and design. The life cycle concept, the importance of implementing controls during the planning, analysis, design, implementation and evaluation phases of a management information system to solve business management problems are highlighted.
By the end of this course, you will be able to:
- Describe the development of the life cycle of information systems.
- Compare the different methods and tools used in systems analysis and design.
- Describe the architecture and functions of database management systems.
- Use currently popular database management systems.
- Analyze information requests and write advanced SQL queries that produce the requested information.
- Describe the responsibilities of a database administrator.
- Analyze and document current business processes and systems using diagramming tools.
- Participate as a team member in the analysis and documentation of a business process.
This course surveys information security essentials needed for a foundational understanding of the Information Security discipline from the business level perspective. Common attacks and vulnerabilities against an organization will be identified and deliberated. Furthermore, the course provides a survey of how to mitigation the risk of attack, the managerial and legal requirements on organizations including reporting requirements, the professional ethics surrounding cybersecurity, and how these affect security policy formation and implementation.
Prerequisite: MIS 1500
By the end of this course, you will be able to:
- Understand common security vulnerabilities and attached that organizations face in the information age.
- Analyze security threats posed by the use of e-commerce technology for end-users and enterprises.
- Analyze the technology available to combat e-commerce security threats.
- Evaluate IT/Technology security management processes.
- Evaluate methods to mitigate risks, managerial and legal requirements, and ethical concerns of organizations in the information age.
- Create a robust incident response, disaster recovery and business continuity plans.
This course provides students with the fundamental concepts of information and cybersecurity. Specific topic areas covered include integrity, availability and confidentiality of data. Students will gain a fundamental knowledge of risk management, governance, cryptography and network security. Other topic areas include business continuity and legal issues. Students will also be introduced to major security incidents and cybersecurity trends. The threats and vulnerabilities organizations are facing as well as the tools and techniques used to secure them.
By the end of this course, you will be able to:
- Demonstrate foundational knowledge of cybersecurity principles
- Discuss the concepts relating to information security management, including confidentiality, integrity, and availability (CIA), vulnerabilities and threats, risks, and countermeasures.
- Define the common principles of cybersecurity management control.
- Develop security mechanisms that can be put into place to compliment nontechnical management controls.
- Discuss the current national legislation, regulations and standards that affect information security management, cybersecurity, information assurance and information governance.
- Explain cryptography and identify the tools for implementing core security services upon which all information security technologies are built.
Key topic areas include securing cyber-physical systems and maintaining an effective security operations program. Specific topics for this course include interconnected systems, sensors and devices. Students will analyze the inherent risks of cyber-physical systems will learn how to develop properly secured systems. The broader operations of cyber-physical security including maintaining policies, auditing, configuration/change management and vulnerability assessment will also be analyzed.
Prerequisite: MIS 1300
By the end of this course, you will be able to:
- Demonstrate comprehension of the concepts used in physical security planning.
- Implement physical security measures.
- Develop protection mechanisms to safeguard sensitive information and preserve essential secrecy.
- Analyze physical security planning documents and their purposes.
- Discuss the operational security five-step process:
- Identify critical information
- Determine threats
- Analyze vulnerabilities
- Assess risks
- Apply appropriate countermeasures
- Develop a plan to strengthen the people component of information security programs.
- Explain the 3 general categories that security controls fall under (physical, technical and operational controls).
- Discuss practical and proven techniques for effectively conducting security assessments.
An introduction to network security and cryptography. Specific content areas for this course are network services, devices, configurations and the vulnerabilities and threats within a system. Knowledge and experiential learning provided in this class includes detection and intrusion prevention of common attack types and designing network security architecture using tools such as firewalls and honeypots. Students will also gain fundamental knowledge of encryption methods, symmetric/asymmetric systems, cryptography and hashing. Students will gain hands on experience through red team blue team lab scenarios.
Prerequisites: MIS 1300, MIS 2140 and CYB 2100
By the end of this course, you will be able to:
- Demonstrate proper network hacking and scanning techniques to evaluate security vulnerabilities across an entire network.
- Demonstrate proper use of authentication and encryption methods.
- Identify the various types of firewalls that are available and discuss the threats each helps mitigate.
- Apply network monitoring tools to discover and identify potential hackers and malware.
- Demonstrate the ability to access a target location using various covert and overt methods.
- Test and evade all security control types: logical, physical and administrative.
- Apply defensive security techniques, including network analysis training sessions and incident response drills.
This course further develops student skills through hands-on lab exercises that build upon the concepts learned in CYB 3200. Red team blue team scenarios will be used to reinforce hacking methodologies used to assess and attack a target computer system. Key topic areas include attack exploits and using security tools and techniques to find and fix vulnerabilities. Students engage in red team/ blue team exercises stressing ethical hacking and penetration testing. (Prerequisites CYB3200, CYB3300)
By the end of this course, you will be able to:
- Analyze the stages an ethical hacker takes in order to compromise a targeted system.
- Demonstrate the ability to install, configure, use and manage hacking software.
- Demonstrate foundational knowledge of cybersecurity policy and strategy concepts.
- Create cybersecurity and strategic policy documentation.
- Apply vulnerability analysis to identify network security loopholes.
- Analyze current global cybersecurity issues and how the errors made by users, administrators, or programmers can lead to exploitable insecurities.
The capstone course for the Cybersecurity program is designed to consolidate the business and cybersecurity knowledge acquired during the completion of the program. The skills, tools and best practices used to effectively manage a cybersecurity project from its inception to successful closure will be discussed. Students will manage a cybersecurity project that improves the security posture of an organization. Students will apply project management and cybersecurity best practices as they work through the project life cycle. This course promotes the development of consultative communication skills and interpersonal skills with team members and other project stakeholders.
Prerequisite: CYB 4100
By the end of this course, you will be able to:
- Implement solutions to secure computer systems and networks
- Perform a digital forensic investigation of real-world case
- Identify and assess cybersecurity threats.
- Defend against cyberattacks
- Detect, triage and mitigate cybersecurity breaches
CYBERSECURITY B.S. CORE COURSE DESCRIPTIONS (24 CREDITS)
The courses below are heavy in application.
Advances the students’ knowledge of programming concepts and design principles acquired in MIS 2140. Students will develop more advanced algorithms and use more complex data structures. Concepts of GUI, web-enabled and event-driven programming will be utilized.
Prerequisite: MIS 2140
By the end of this course, you will be able to:
- Incorporate information stored in a database into an application.
- Identify the elements of graphical user interface programming.
- Use controls and audit trails in programming.
- Develop web-based programs using programming tools.
- Develop programs requiring the use of more complex data structures.
- Develop a more thorough understanding of the complete process of program development.
- Write programs that interact with databases and the web.
In this course, students learn how to perform data analysis, identify vulnerabilities and automate large scale network attacks, along with other cybersecurity scripting opportunities. Fundamentals of scripting for security testing, data analysis and other routine IT tasks are explored.
Prerequisite: MIS 2140
By the end of this course, you will be able to:
- Discuss the native libraries and bindings available specifically for penetration testing and other cybersecurity tasks.
- Develop custom scripts to generate high volume attack traffic for vulnerabilities testing.
- Create scripts to perform data analysis from log events; identify potential vulnerabilities in software; and automate large-scale network attacks, extract metadata and investigate forensic artifacts.
- Develop code to intercept and analyze network traffic.
- Construct packet sniffers.
- Perform post-exploitation activities.
Students work independently and collaboratively to develop the complex skills necessary to design, create and maintain reliable and secure services, devices and applications in various networked environments. Through exploration and application of troubleshooting, administration and efficiency standards, students develop skills in network analysis. Additional topics include congestion control, switching, routing, analysis and design of network protocols (both wired and wireless), data centers, analysis and performance of content distribution networks, network security, vulnerability and defenses, net neutrality, and online social networks.
Prerequisite: MIS 1300
By the end of this course, you will be able to:
- Discuss virtualization technologies.
- Perform switching and routing process.
- Discuss and use Domain Name System (DNS) processes
- Perform DHCP and static IP Addressing procedures
- Explain standards for and operation of virtual private networks (VPN) and virtual local area networks.
In this course, software-defined networking (SDN) and increasing the agility and flexibility of networks are explored. Students learn how to improve network control by enabling enterprises and service providers to respond quickly to changing business requirements and how to manage an SDN deployment. SDN concepts and components are used to create through-modeling in an open networking platform that enables SDN and constructs a solid foundation for network functions virtualization (NFV) for all network sizes.
Prerequisite: CYB 2300
By the end of this course, you will be able to:
- Discuss software-defined networking.
- Explain and Analyze OpenFlow/ SDN control concepts.
- Apply virtualized switching concepts
- Apply virtual routing concepts.
- Apply SDN principles to solve network problems.
- Use application program interfaces (API) to relay information to switches and routers.
- Develop a virtual network.
Students examine cryptographic systems, including how to properly utilize these systems in real-world scenarios. Concepts include using shared keys to provide secure communication when adversaries attempt to manipulate and listen to network traffic. Research of deployed protocols to analyze mistakes in existing systems is conducted. Students apply public-key techniques to generate shared secret keys, which allow for secure communication. Students also explores advanced cryptographic skills, such as zero-knowledge, privacy mechanisms and other forms of encryption.
Prerequisite: MIS 1300
By the end of this course, you will be able to:
- Perform current cryptography methods.
- Discuss how crypto-primitives work.
- Discuss and perform encryption key standards.
- Identify and discuss basic key exchange methods.
- Discuss and identify data integrity issues.
- Apply techniques to analyze data integrity.
- Examine authenticated encryption standards.
- Analyze the role of digital signatures and certificates in the authentication of data.
Digital forensics explores the concepts and tools necessary for computer forensics. Students learn how to conduct investigations to correctly gather, analyze and present digital evidence to both business and legal audiences. Students examine the tools to locate and analyze digital evidence on a variety of devices, how to maintain up-to-date skills to work with changing technologies and about digital forensics laws and regulations.
Prerequisite: CYB 3000
By the end of this course, you will be able to:
- Perform digital forensics, the science of investigating cybercrimes.
- Employ fundamental computer forensic practices.
- Identify and apply current laws and procedures associated with digital evidence collection
- Examine the relationships between incident categories, evidence handling and incident management.
- Evaluate the effectiveness of digital forensic tools.
- Perform basic computer forensic analysis.
This course builds on concepts learned in CYB 3300. Students discuss various topics that include securing cyber-physical systems and maintaining an effective security operations program. Analysis of the inherent risks of cyber-physical systems and development of properly secured systems are completed. Students also explore operations of cyber-physical security, such as maintaining policies, auditing, configuration/change management and vulnerability assessment. Scripts to parse logs, conduct penetration testing and perform other cybersecurity tasks are developed.
Prerequisite: CYB 3300
By the end of this course, you will be able to:
- Build an effective threat hunting solution based on open-source tools.
- Demonstrate ability to find and investigate malware, phishing, lateral movement, data exfiltration and other common threats.
- Apply scripting knowledge to create scripts for parsing logs, conducting penetration testing and managing other cybersecurity tasks.
- Evaluate the effectiveness of the zero-trust security framework.
- Apply foundational knowledge of the MITRE ATT&CK framework to structure intelligence about adversary behavior.
- Examine DNS sinkholes to help battle malicious software (malware and spyware) in networks.
This survey course will introduce students to the concepts and principles of Data Mining that supports the industry-standard CRISP-DM model. The model includes Data storage and preparation, database management, data visualization, and data-driven decisions for solving business problems.
Prerequisites: MIS 1500 and MTH 2310
By the end of this course, you will be able to:
- Recognize the opportunity and challenges of Big Data analysis
- Use Data Warehouse methodology to import, cleanse and reduce a large data set.
- Use software to explore, visualize and build a model from the data.
- List, describe and apply data mining solutions such as classification problems, clustering, co-occurrence and causal conclusions.
- Develop the ability to present a model to a business team; illustrates business understanding and modeling.
- Understand the concept of Predictive modeling.
- Critique a project proposal.

ADMISSION
APPLICATION PROCESS
The program follows a simple 3-step application process. The step-by-step process is outlined below.
STEP 1: SUBMIT APPLICATION
Candidates can apply to the program online and attach all required materials as outlined in the requirements below.
STEP 2: ROLLING ADMISSION
The admissions team will assess your application as soon as it is received.
STEP 3: INTERVIEW
Candidates might be required to give an interview before being accepted into the program. Once all the requirements are completed, the admissions team will notify you with a decision.
For admissions support, we offer online office hours, an admissions checklist, and email and phone support to answer your questions.
APPLICATION REQUIREMENTS
Applicants for the undergraduate program are required to have:
- Passport ID page (must be valid for at least 6 months beyond the entry date to Northwood University)
- Secondary school transcripts
- Secondary school completion certificate or diploma
- College or university transcripts (if you have completed any university credits)
- English proficiency
KEY DATES
- Please Note: Application fee is refunded only in the case an applicant is not offered admission to the program.
OPTIONAL PRACTICAL TRAINING – US OPT
After you have completed at least one year of your studies in the U.S. you will be eligible to participate in the US OPT (Optional Practical Training) program for F-1 students upon the completion of your undergraduate degree, allowing you to stay in the US while you start your career in information systems and cybersecurity.
Optional Practical Training (OPT) is temporary employment in the US that is directly related to an F-1 student’s major area of study. Eligible students can apply to receive up to 12 months of OPT employment authorization before completing their academic studies (pre-completion) and/or after completing their academic studies (post-completion). Please click here to know more about OPT.
Northwood’s Bachelor of Science in Information Systems and Cybersecurity program is a STEM (Science, Technology, Engineering, and Mathematics) certified program for Optional Practical Training (OPT) purposes. This allows the graduates of the program to apply for an additional 24 months of extension of OPT. Ultimately, it offers the potential for international students to work in the US for a total of 3 years and the potential for a work visa (H1-B, etc.)

TUITION & SCHOLARSHIPS
TUITION AND FEES
The following figures are fixed 2024-2025 costs for 12-17 credit hours per semester.
| Expense Description | 1st Semester (Fall) | 2nd Semester (Spring) | Total Per Year |
|---|---|---|---|
| Tuition* | 1st Semester (Fall): $16,400 | 2nd Semester (Spring): $16,400 | Total Per Year: |
| Student and Technology Fee | 1st Semester (Fall): $800 | 2nd Semester (Spring): $800 | Total Per Year: $1600 |
*The fee does not include transport expenses, health insurance, any associated visa fees etc. and accommodation. It also does not cover any other expenses that are not expressly mentioned above. Students are required to live on campus for the first two years of attendance at Northwood University.
Healthcare plan is mandatory and is available for approximately USD $1,500*/year (*Subject to change per academic year).
SCHOLARSHIPS
The aim of the scholarships is to provide outstanding candidates with an opportunity to study irrespective of their financial circumstances. The program offers significant scholarship funding to the most talented applicants.
All applicants for the Bachelor of Science in Information Systems and Cybersecurity program are automatically considered for Northwood University scholarships. Scholarship amounts will be noted in your letter of acceptance.

PROGRAM EXPERIENCE
With a large international presence both at our U.S. locations and abroad, the Northwood student body is very diverse. Our alumni are at ease in complex, multi-cultural business environments with a professional network around the world. Learning at Northwood takes place in more than just the classroom. With a multitude of activities to choose from, students realize significant personal and professional growth which, after graduation, will set them apart as they launch their careers.
CAMPUS LIFE

Be it academic-based organizations like the Entrepreneurship Society, Collegiate DECA or Business Professionals of America (BPA) to Greek Life to service-based organizations like Circle K, Rotaract, the Student Athletic Advisory Council or Student Government Association, Northwood University has ways for students to be engaged and involved on campus and in the local community. These experiences help students learn first-hand, how businesses and people connect through shared experiences.
PROFESSIONAL DEVELOPMENT

Northwood students graduate with a superior business education that gives them a foundation of understanding free markets, entrepreneurial endeavors, personal responsibility, and ethical behavior. And, NU students also graduate with the ability to effectively communicate their ideas, beliefs, and experiences in an effort to promote success in their own lives and in the lives of others. Through workshops and campus-life programming, students hone networking, interviewing and résumé writing skills putting them one more step ahead in a competitive job market.
EXPERIENTIAL LEARNING

One hallmark of the Northwood education is hands-on, experiential learning. Many of our academic programs enhance classroom learning with large-scale, active learning student-run projects. These events allow our students to apply what they learn in the classroom to real situations.
ENTERPRISE/ENTREPRENEURIAL ORIENTATION

Many Northwood alumni earn their livelihoods in enterprises they own in whole or in part. While we offer a program in entrepreneurship, our entire curriculum is focused on enterprise models and entrepreneurial achievements. Enterprise is a key tenet of our Mission, and we believe entrepreneurship is the essential element of our free market economy.
COMPETITIVE ADVANTAGE

While our student-athletes are competing on the athletic fields as part of the NCAA Division II Great Lakes Intercollegiate Athletic Conference (GLIAC); many of our students also compete in academic arenas. Our national champion Mock Trial team has bested teams from Harvard, Georgetown, and Stanford while our Competitive Speech team, American Marketing Association, BPA, DECA, and American Advertising Federation student chapters regularly place in regional and national competitions.

ABOUT NORTHWOOD
On March 23, 1959, two young men with an idea, a goal, and a pragmatic philosophy to encompass it all, broke away from their careers in a traditional college structure to create a new concept in education.
Their visionary idea became a reality when Dr. Arthur E. Turner and Dr. R. Gary Stauffer enrolled 100 students at Northwood Institute. They envisioned a new type of university – one where the teaching of management led the way. While the frontiers of space were revealing their mysteries, Stauffer and Turner understood all endeavors – technical, manufacturing, marketing, retail, every type of business – needed state-of-the-art, ethics-driven management.
Time has validated the success of what these two young educators called "The Northwood Idea" – incorporating the lessons of the American free-enterprise society into the college classroom.
The University grew and matured; Northwood went from being an Institute to an accredited University, the DeVos Graduate School of Management was created and then expanded; the Adult Degree Program and its program centers expanded to over 20 locations in eight states; international program centers were formed in Malaysia, People's Republic of China, Sri Lanka, and Switzerland; and significant construction like the campus Student Life Centers added value to the Northwood students' experience. New endeavors such as Aftermarket Studies, entertainment and sports management and fashion merchandising, along with a campus partnership in Montreux, Switzerland, demonstrate an enriched experience for all our students.
Northwood University educates managers and entrepreneurs – highly skilled and ethical leaders. With more than 65,000 alumni and a vibrant future ahead, The Northwood Idea is thriving.
NORTHWOOD FACTS
|
18+ |
athletic teams |
|
31% |
of Northwood graduates own some or all of their business |
|
$13m |
in scholarships available |
|
40+ |
clubs, fraternities and sororities |
|
82% |
of graduates employed full-time or accepted to graduate programs (as per our most recent graduate survey) |
18+
athletic teams
31%
of Northwood graduates own some or all of their business
$13m
in scholarships available
40+
clubs, fraternities and sororities
82%
of graduates employed full-time or accepted to graduate programs (as of our most recent graduate survey)

ACCREDITATIONS, APPROVALS, AND MEMBERSHIPS
Northwood University believes it has a responsibility to its students and the industries and communities it serves to provide the highest standard of educational excellence possible. One measure of how well an educational institution meets this responsibility is in its accreditations and approvals by outside education associations and governmental interests. Because each Northwood location is served, at least partially, by different governmental agencies and academic accrediting bodies, and because all have been in existence for varying lengths of time, the accreditations and approvals may vary from one location to another.
ALL NORTHWOOD UNIVERSITY CAMPUSES/LOCATIONS HAVE THE FOLLOWING ACCREDITATIONS AND APPROVALS:
- Northwood University is accredited by the Higher Learning Commission (www.hlcommission.org). For more information, please click here.
- Northwood University business degree programs have business specialty accreditation from the Accreditation Council for Business Schools and Programs (ACBSP), (www.acbsp.org).
- The United States Department of Homeland Security (DHS) certified school for nonimmigrant foreign students (Fvisa); Citizenship and Immigration Services (USCIS)/ Immigration and Customs Enforcement (ICE); and Student and Exchange Visitor Program (SEVP) as a higher education institution for international students.
- Respective state offices for Veterans Administration programs as a higher education institution for degree-seeking qualified veterans and dependents.
- The U.S. Bureau of Internal Revenue as a tax-exempt institution as provided for in Section 501 (c) (3) and other applicable parts of the Internal Revenue Code for higher education organizations.
NORTHWOOD UNIVERSITY MEMBERSHIPS ARE REPRESENTED IN SUCH EDUCATIONAL AND PROFESSIONAL ORGANIZATIONS AS:
- American Accounting Association
- American Advertising Federation
- American Association of Collegiate and Admissions Officers Registrars
- American Certified Fraud Examiners
- American College Health Association
- American College Personnel Association
- American Hotel and Lodging Association
- American Institute of Certified Public Accountants
- American Library Association
- American Management Association
- American Marketing Association
- American Marketing League Association
- American Payroll Association
- American Taxation Association
- Association for Communications Technology Professionals in Higher Education
- Association for Higher Education and Disability
- Association for Leadership Educators
- Association for the Tutoring Profession
- Association of College and Research Libraries
- Association of College and University Housing Officers International
- Association of College and University Telecommunications Administrators
- Association of Professional Researchers for Advancement
- Association of University Programs in Health Administration
- Association of Veterans Educators Certifying Officials
- Automotive Aftermarket Industry Association
- College and University Personnel Association for Human Resources
- Council for the Advancement of Experiential Learning
- Council for Higher Education Accreditation
- Council for Hotel and Restaurant and Institutional Education
- Data Processing Management Association
- Educause
- Family Enterprise Research Scholars
- Family Firm Institute
- Global Consortium of Entrepreneurship Centers
- Intercollegiate Press Association
- International Assembly for Collegiate Business Education
- International Council on Hotel, Restaurant & Institutional Education
- International Leadership Association
- Mathematical Association of America
- Motor and Equipment Manufacturing Association
- National Academic Advising Association
- National Advertising Federation
- National Association for Campus Activities
- National Association for College Admission Counseling
- National Association for Developmental Education
- National Association of College Admissions Counselors
- National Association of College Auxiliary Services
- National Association of College Stores (through its bookstore provider)
- National Association of College and University Business Officers
- National Association of Colleges and Employers
- National Association of Educational Buyers
- National Association of Independent Colleges and Universities
- National Association of Intercollegiate Athletics
- National Association of International Educators
- National Association of Graduate Admissions Professionals
- National Association of College and University Mail Services
- National Association of Student Financial Aid Administrators
- National Association of Student Personnel Administrators
- National Association of Veterans Programs Administrators
- National Automobile Dealers Association
- National Collegiate Athletic Association
- National Collegiate Honors Council
- National College Learning Center Association
- National Cooperative Education Association
- National Council of Teachers of English
- National Council of Teachers of Mathematics
- National Council of Women of the United States
- National Association of Educational Buyers
- National Association of Independent Colleges and Universities
- National Association of Intercollegiate Athletics
- National Association of International Educators
- National Home Fashions League
- National Restaurant Association
- Newspaper Association of America
- Organization of American Historians
- Photographers’ Association of America
- Society for College and University Planning
- Society for Human Resources
- Specialty Equipment Market Association
- The Fashion Group
- University Risk Management and Insurance Association